How Security Works in the Ignition Perspective Module

If you’ve visited this blog at all during the past year, chances are you’ve heard about the Ignition Perspective Module. Since releasing the module in April 2019, we’ve told you quite a bit about how Perspective provides powerful new capabilities for building mobile-first industrial applications natively in HTML5 and CSS3. One aspect of Perspective that we haven’t explored in much detail are its security features, so in this blog post I’ll give you a closer look at how we’ve built Perspective with security in mind, right from the very beginning.
Perspective Helps You Turn Data Into Action
First, it’s worth reviewing the main purpose of the Perspective Module, which is to make it easier to turn data into action. In Perspective, you can design industrial applications for any screen size. You can design for mobile, desktop, and display screens all at the same time. You can customize the user experience easily with mobile-optimized container types.
Perspective runs on any smartphone, desktop or other smart device with a modern web browser. Perspective lets you see your entire system at a glance and take control with intuitive touch commands and bidirectional data binding. It lets you leverage mobile-device features like the GPS, accelerometer, camera, barcode scanner (NFC), and touch gestures. And the unlimited Ignition licensing model offers as many clients, tags, connections, and designers as you need.
You can easily deploy unlimited Perspective sessions from anywhere with a single click. Opening a Perspective session is easy: just open your browser, point it to a URL of your server, and the application is available. You can even send secure web links through applications that anyone can use and click on to get access to it in their browser.
Security is Built Into the Foundations of Perspective
Along with these mobile-first capabilities, we've built security into the Perspective Module from the ground up. Perspective supports the federated identity standards OpenID Connect and SAML, and federated identity providers including ADFS, Okta, Duo, and many others. Federated identity providers bring support for two-factor authentication and single sign-on. Perspective also has a permissions model that offers a variety of simple ways to secure your Perspective apps.
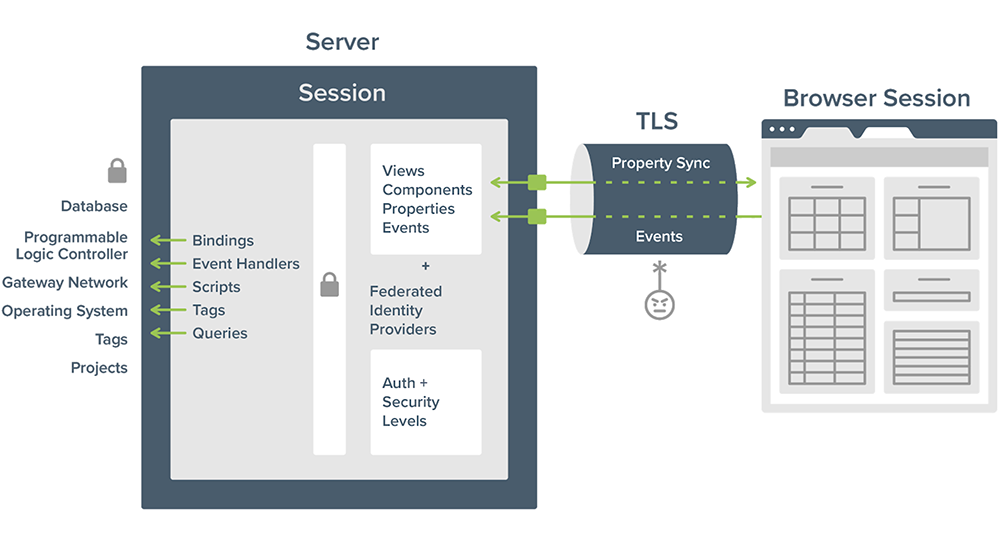
In Ignition Perspective, the application lives on the server and the session runs in the browser. Property syncs and events pass through a TLS-encrypted connection between the browser and the server.
Let’s look at some of the underpinnings of Perspective to get a better look at how security is built right into it. Perspective can deploy mobile clients through the Ignition Perspective App or through web browsers. When you use Perspective in a web browser, you go to a URL, an IP address, or a host name of a server to get access, and then the entire application runs in the browser. Most of the security, however, is handled by the Ignition Gateway rather than by the browser. The Perspective browser session communicates back to the Ignition server to get information; however, it is very limited in how it can interact with the Ignition server. When you open up a Perspective application that you’ve built, you log in and establish a session with the server, so that Ignition can verify who you are before it grants access to any data. Once that session has been established, the entirety of the application basically lives on the Ignition server, including the page that you're on and all of the views, components, properties, events, and models that are represented in the session.
Synchronizing Properties
There are only two points at which the actual Perspective session interacts with the Ignition server, as the diagram above shows. One of those points is for synchronizing properties. Let’s say that you have a tank level component bound to a tag. As the tag property changes, you’d want it to be synchronized to the browser so that the proper level is indicated there, or vice versa. If you were to write to a tag to change the setpoint, then you’d want to let the server know that you’ve changed this particular value, and that is only accomplished through property syncs. Once you synchronize a property, there are whole layers of protection in place to determine whether or not that change can actually occur down to the device.
During a Perspective session, the Ignition server is communicating with a lot of resources such as PLCs or other devices, databases, other Ignition servers through the Gateway Network, the operating system, and any other projects or files, and it’s important to protect all of those connection points. Perspective puts a whole layer of security in front of all those protected resources. When a session is established, the federated identity providers on the server are used to check on who that person is and what permission levels they have. If the user tried to write to a tag, that request would have to go through the security layer on the server to check whether or not they are allowed to do that. If the user doesn't have the correct permission, the sync is rejected.
Responding to Events
The second point where the Perspective session interacts with the Ignition server is when responding to events. For example, when the user clicks on a certain button, the action is to have them upload a file. We want to know that the file was uploaded, and events are also sent to the server so that we can respond to those events with various handlers, and maybe to go and get data or do something with that.
As the diagram shows, the events and property syncs pass through a secure SSL/TLS encrypted connection between the browser and the Ignition server. This is similar to when you log into your bank account online and see “https” in the URL at the top of the screen, which indicates that the website is secured by an SSL/TLS encryption. Because events and property syncs go through this secure connection, it is very, very difficult for a bad actor to do something harmful with them.
By looking at the architecture of Perspective, you can see that we intentionally built it to protect the resources that communicate with the server by setting security layers and verification requirements that prevent bad actors from accessing them.
Four Critical Steps
In order to make this setup as secure as possible, you need to enable some features inside of Ignition. Below are four actions that we recommend you take on the Ignition server in order to secure Ignition in your operating environment:
- First, enable SSL.
- Second, set up proper authorization systems.
- Third, enable auditing.
- Fourth, identify access levels or permissions that define who is allowed to do what in the application.
In the video below, Senior Software Engineer Joel Specht and I walk through each of these important security steps in detail. We recommend that you watch the video and enact these steps as soon as possible.
We also recommend that you review and follow the recommended security steps in the Ignition Security Hardening Guide. By taking basic steps to secure your Ignition installation and the network where it is deployed, regularly maintaining your system, and planning ahead, you’ll be in a much stronger position to avoid system intrusion or business disruption.
